After a lot of surfing and some arguments, I decided to share with you the – in my opinion – top 5 failed domain names. I will enable the comments in this post as it is very funny and I
X-Nerd strikes again
Few days ago the Pakistani hacker ‘X-Nerd’ (x-nerd@live.com) hacked several domains and added a new file in their root called ‘x.php’. Few sites that are still having this file while I am writing this post are:
http://aeciecuador.org/x.php
http://clipartbackgrounds.net/x.php
http://ieducationaltoys.com/x.php
http://vectorpanic.net/x.php
and many more
This time X-Nerd hacked Panda Security Pakistan. A company that offers security has been hacked, this is not a good promotion for their products
Anonymous developed U.R.G.E.

Anonymous released a new tool to hijack trending topics on twitter. It is called Universal Rapid Gamma Emitter or simply U.R.G.E. It helps the user to post tweets on a trend without having to copy paste trending topic manually. Don’t be afraid to download it, it does not contain any malicious code and it is not an exploit. You can see download information and instructions in source
Windows AUTOPWN

Windows AUTOPWN or winAUTOPWN allows you to autohack targets with minimum interaction. It is an auto shell gaining tool created by quakerdoomer (Azim Poonawala). Even though some antivirus could detect it as a malicious software, it is not. It uses several exploits publicly available and it can be used to test the effectiveness of IDS/IPS
Walking hurts anonymity

As we all know, we can be identified by nearly anything. There is face recognition, voice recognition, fingerprints, DNA, all sorts of biometrics and now they want to add footprints as well. Footprints are as good as fingerprints for identification but it is not only that. The way bare foot hits and leaves the ground while walking creates foot-pressure patterns and those patterns can be used to reveal your identity
Registry Decoder
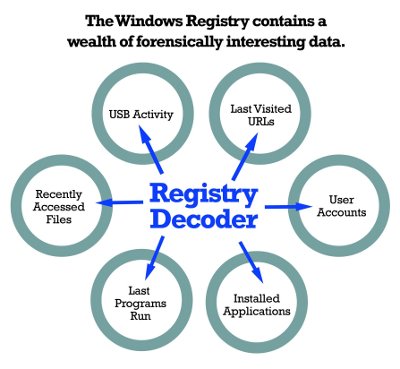
If you use windows then you should know that almost everything you do is recorded. Most of the information can be found on windows registry. It has a list with last accessed files, a list with the last programs run, all installed programs, USB activity, user accounts, last visited URLs, a list of the programs that run when the operating system starts and more. With Registry Decoder you can see all that information, it provides acquisition, analysis, and reporting of registry contents
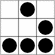
Decipher This – 001

Here we are, my first challenge is a ciphered text. I believe that this is an easy one so I will not help you with hints. If you decipher the following text you will know what to do next, if not, wait for the next one
New Category Created
I am starting a new category called “Challenges”. In this category I will post some challenges (Yes, I know that it is obvious!) that I have found on the Internet in the past few years and some new (I hope). I have solved most of them and I enjoyed it a lot. Some people do not appreciate the solving process and how much you can gain from it. The more difficult the problem the more satisfaction you get. It is not only about the satisfaction but I have learned several things while solving them and most of them were very valuable
BackBox Linux 2 – A must-have for security experts

BackBox Linux version 2 has been released. BackBock is based on Ubuntu and it is used (mostly) by security experts to perform penetration tests and security assessments. It is fast, easy and it has a desktop environment. There are tools for sniffing, spoofing, password cracking, vulnerability scanning, wireless analysis and more
Alloy produces hydrogen using sunlight
A semiconductor material can be altered and used to produce hydrogen from water using sunlight. The research was funded by the U.S. Department of Energy and the results are published in the Physical Review Journal. The antimony-gallium nitride alloy uses solar light energy to extract hydrogen and oxygen by slitting water molecules